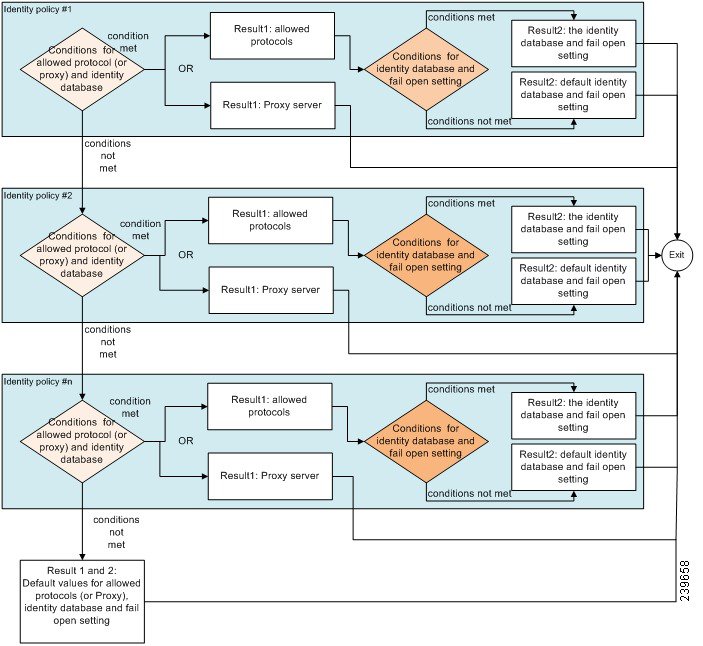
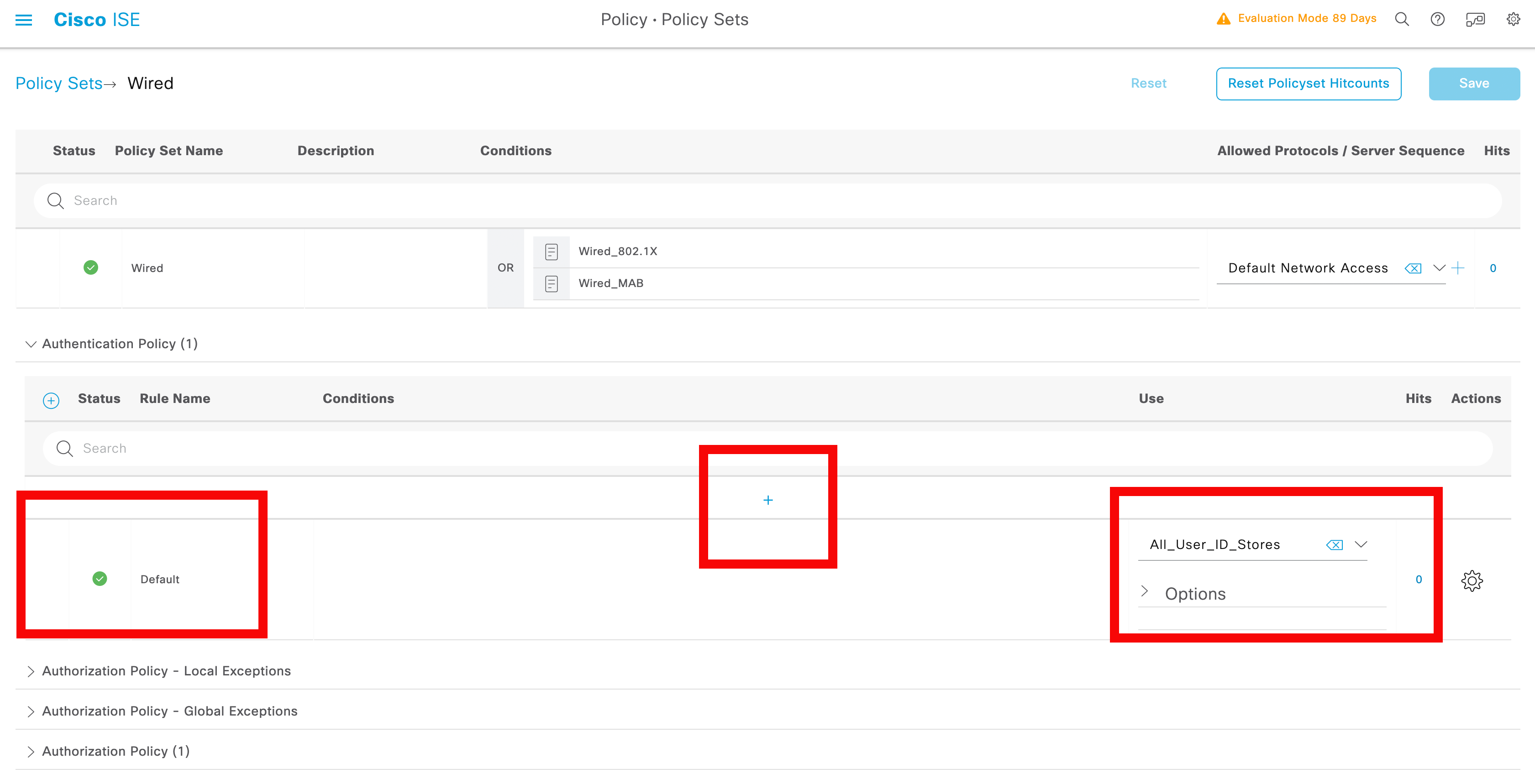
![Cisco Identity Services Engine Administrator Guide, Release 3.1 - Segmentation [Cisco Identity Services Engine] - Cisco Cisco Identity Services Engine Administrator Guide, Release 3.1 - Segmentation [Cisco Identity Services Engine] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/400001-500000/440001-450000/449001-450000/449943.jpg)
Cisco Identity Services Engine Administrator Guide, Release 3.1 - Segmentation [Cisco Identity Services Engine] - Cisco
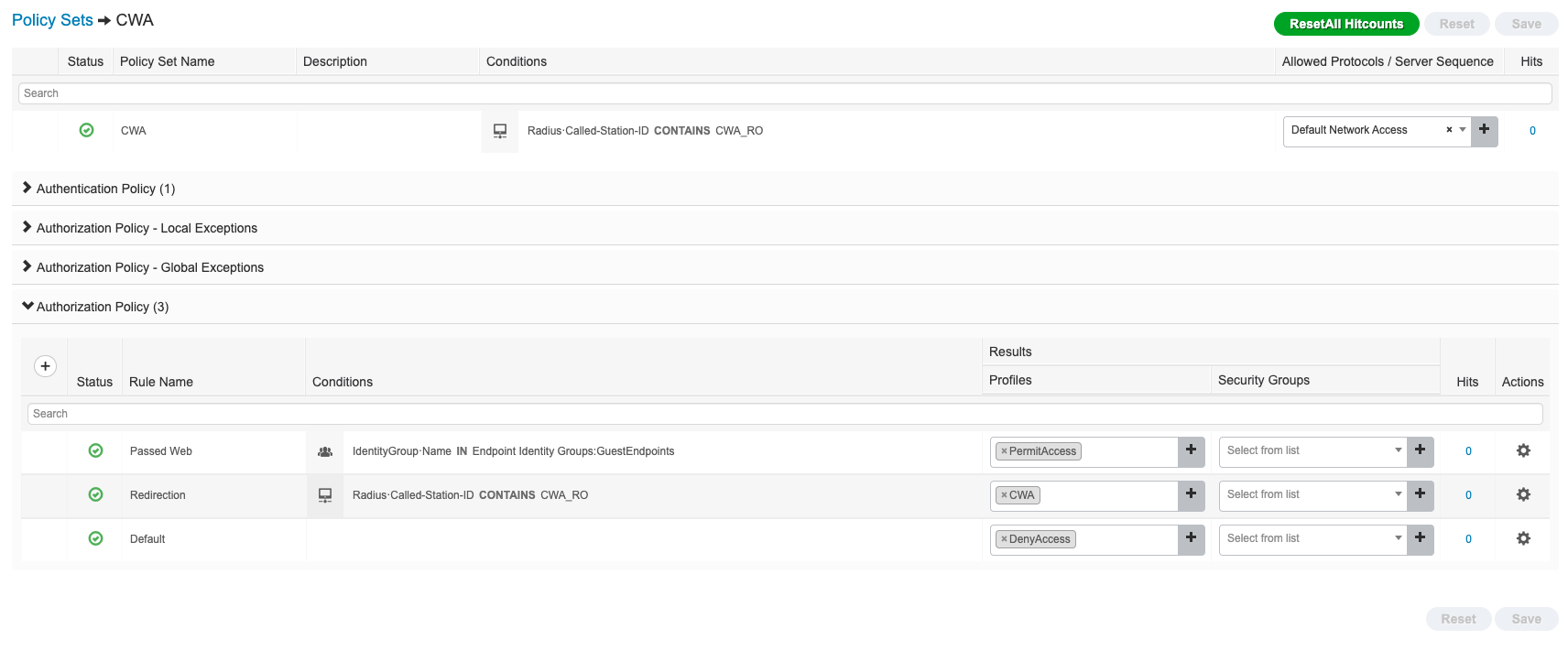
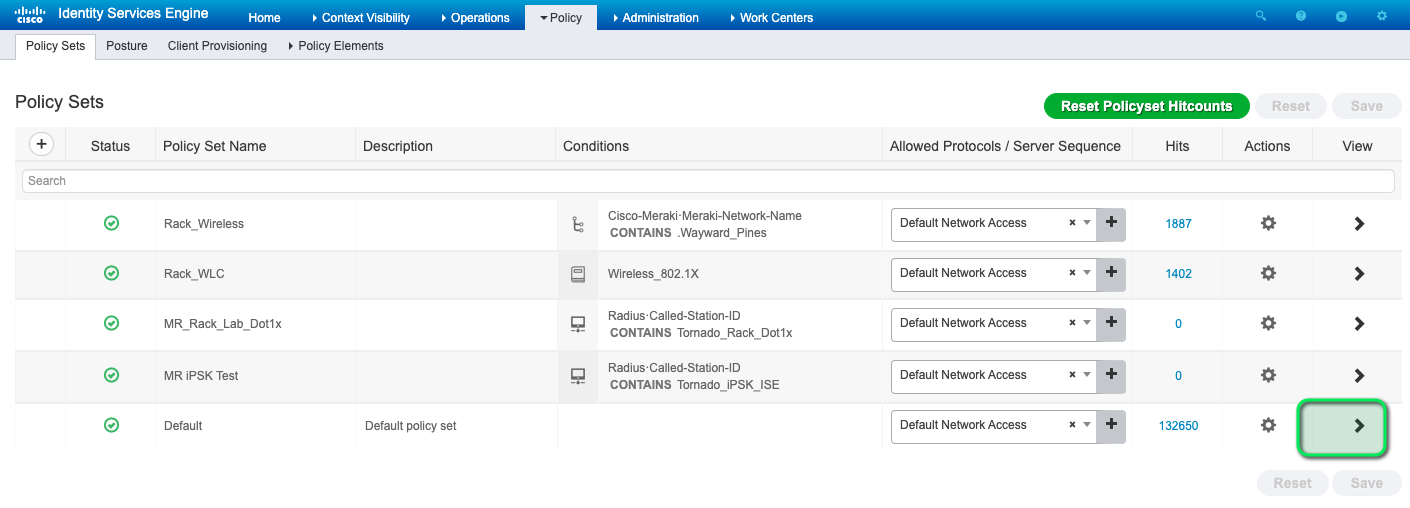
![Cisco Identity Services Engine Administrator Guide, Release 3.1 - Segmentation [Cisco Identity Services Engine] - Cisco Cisco Identity Services Engine Administrator Guide, Release 3.1 - Segmentation [Cisco Identity Services Engine] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/400001-500000/440001-450000/449001-450000/449940.jpg)
Cisco Identity Services Engine Administrator Guide, Release 3.1 - Segmentation [Cisco Identity Services Engine] - Cisco

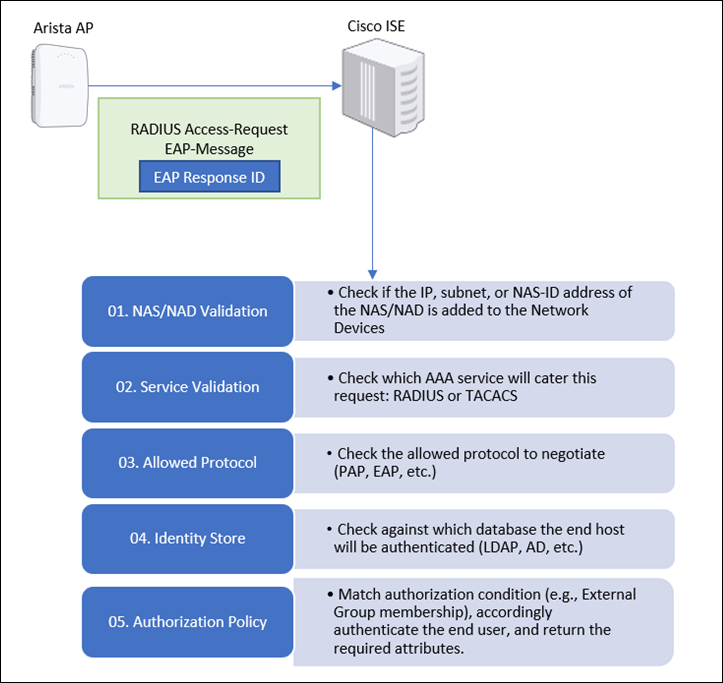
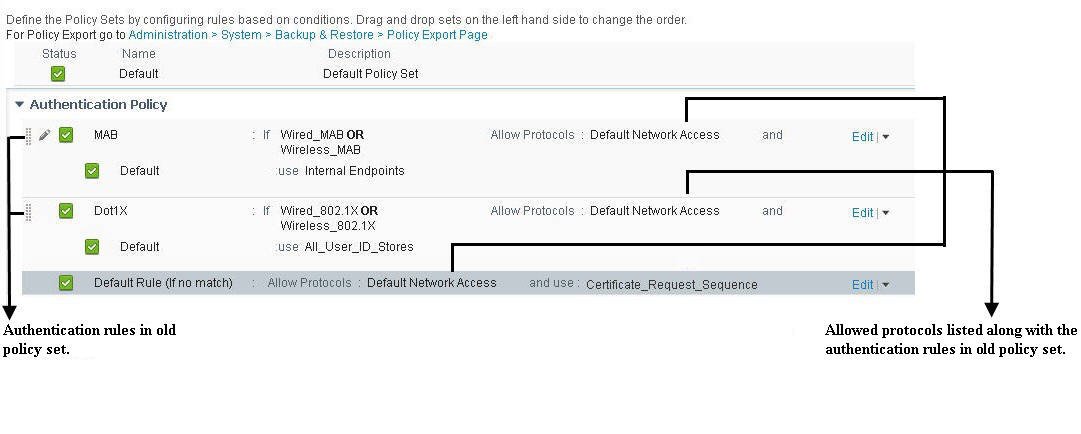
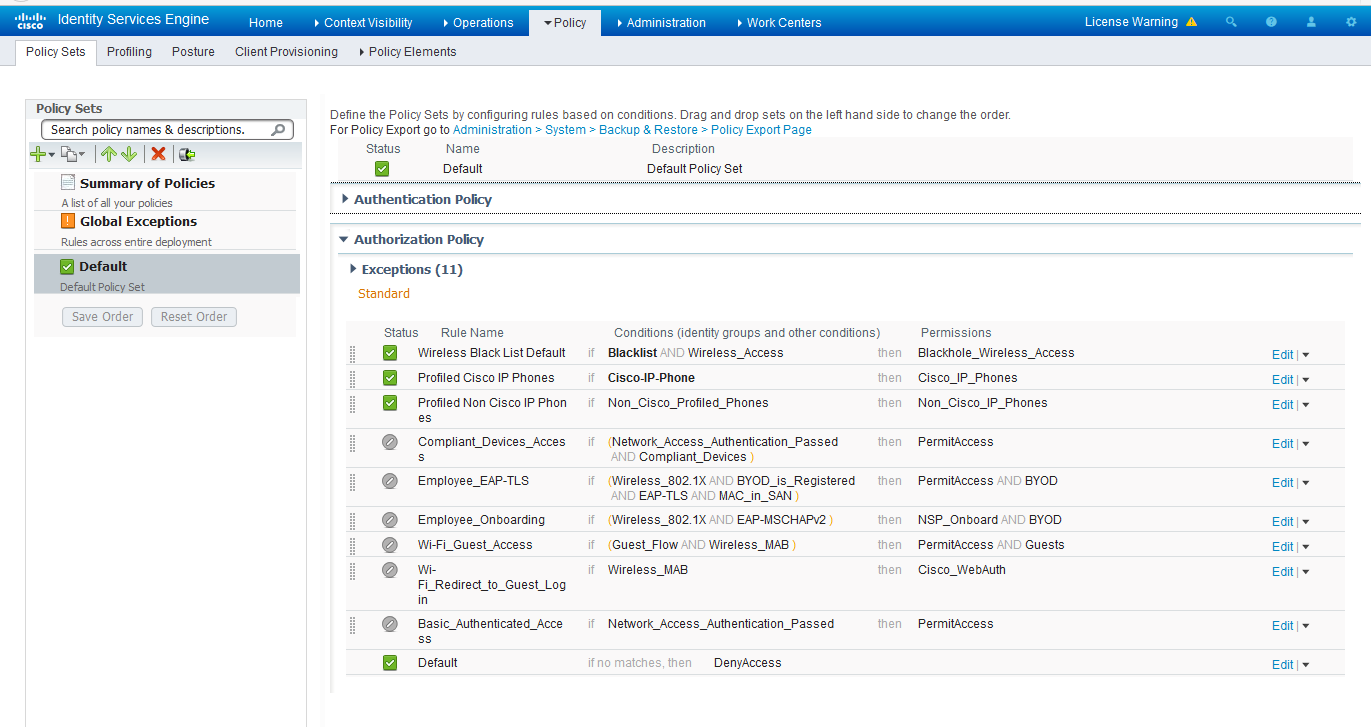
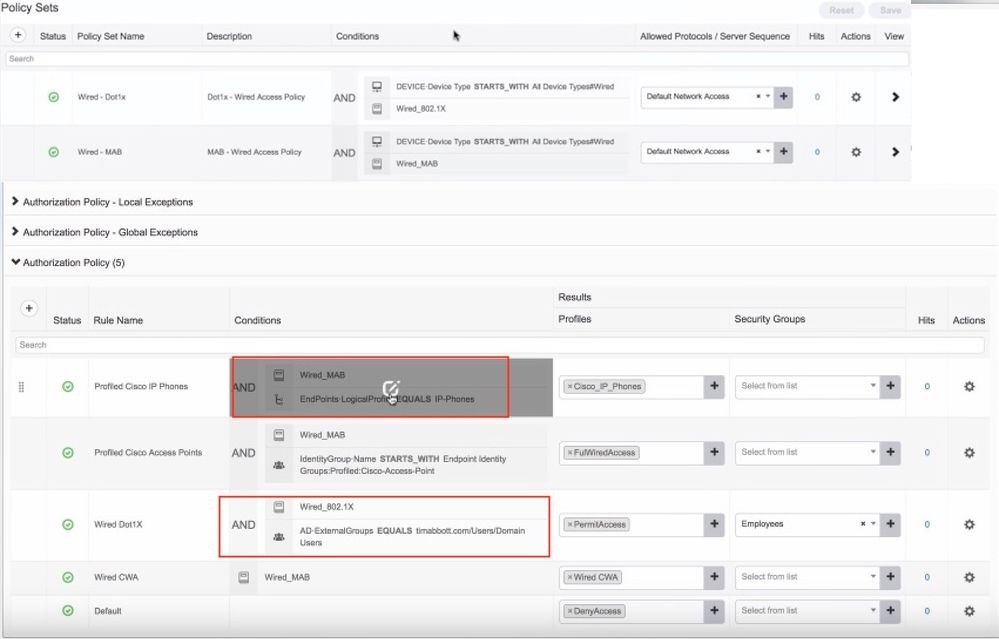
Understanding Authentication Policies > Authentication and Authorization Policies: Using Cisco Identity Services Engine in a BYOD World | Cisco Press

Understanding Authentication Policies > Authentication and Authorization Policies: Using Cisco Identity Services Engine in a BYOD World | Cisco Press