Practical Reverse Engineering: x86, x64, ARM, Windows Kernel, Reversing Tools, and Obfuscation : Dang, Bruce: Amazon.fr: Livres
Layered obfuscation: a taxonomy of software obfuscation techniques for layered security | Cybersecurity | Full Text
GitHub - Dgeeth9595/Android-Obfuscation-Tools: Android Obfuscation tools that work at dalvik bytecode level.
![gives another classification of the obfuscation techniques [40], [14]... | Download Scientific Diagram gives another classification of the obfuscation techniques [40], [14]... | Download Scientific Diagram](https://www.researchgate.net/publication/260791086/figure/fig2/AS:911070004789248@1594227424159/gives-another-classification-of-the-obfuscation-techniques-40-14-based-upon-how-the.png)
gives another classification of the obfuscation techniques [40], [14]... | Download Scientific Diagram


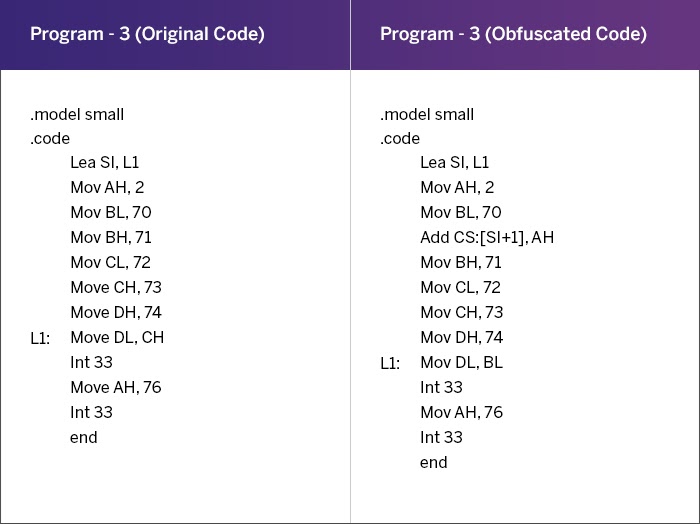


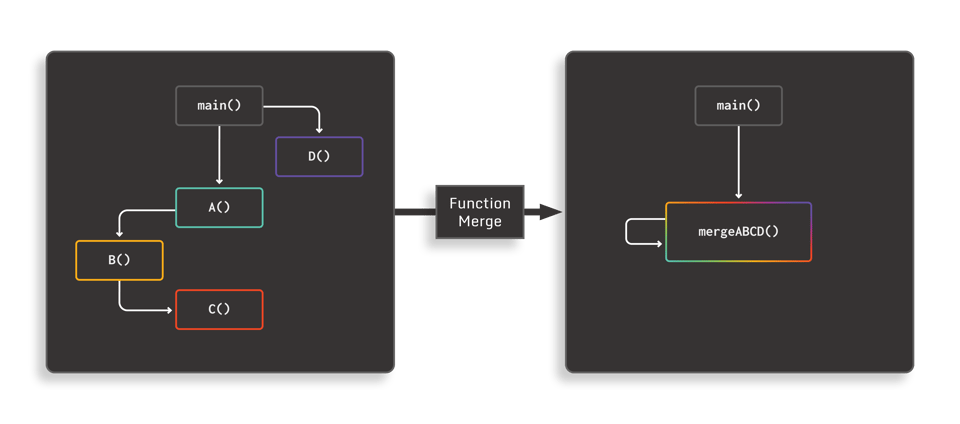



![On the evaluation of android malware detectors against code-obfuscation techniques [PeerJ] On the evaluation of android malware detectors against code-obfuscation techniques [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-1002/1/fig-3-full.png)